What is Third-Party Risk Management? A Comprehensive Guide

In the rapidly evolving digital landscape, where sophisticated threats abound, comprehending and mitigating third-party risks weigh heavily on the minds of risk managers. With 71% of organizations noting an increase in vendors within their third-party network compared to three years ago, addressing this aspect of risk management has come to a critical head.
Third-party risk management (TPRM) involves the process of identifying, assessing, and mitigating risks associated with external or third-party vendors, suppliers, and service providers within your business’s supply chain. As businesses increasingly rely on these external partners to enhance efficiency and competitiveness, the potential for cybersecurity threats also grows. Recent third party data breaches have highlighted the need for effective TPRM to safeguard sensitive data, ensure regulatory compliance, and protect the integrity of business operations against the backdrop of sophisticated cyberattacks.
Third-party risk management within a comprehensive cybersecurity management program assesses all security aspects involved in outsourcing to third parties, encompassing risk criteria establishment and third party partner and vendor onboarding and screening. Let’s explore what is third party risk management!
The importance of third-party risk management

The majority of businesses today work in conjunction with various third-party vendors. Their day-to-day operations often depend on these external relationships for needs like supply chain management and resource development. These partnerships are necessary to remain competitive in the marketplace, regardless of industry. Third-party vendors allow for greater convenience, faster production speeds, and lower costs.
However, these external relationships pose a significant cybersecurity threat to a business if unchecked. Every outside partnership risks opening the door to malicious actors invading their network and gaining access to sensitive information. Third-party risk management (TPRM) is crucial in cybersecurity strategies to safeguard sensitive data and intellectual property accessed by third parties.
Recent third party data breaches, such as those involving major corporations, highlight the importance of managing these risks. Implementing strong TPRM practices is essential for a robust cybersecurity strategy.
The impact of cyberattacks
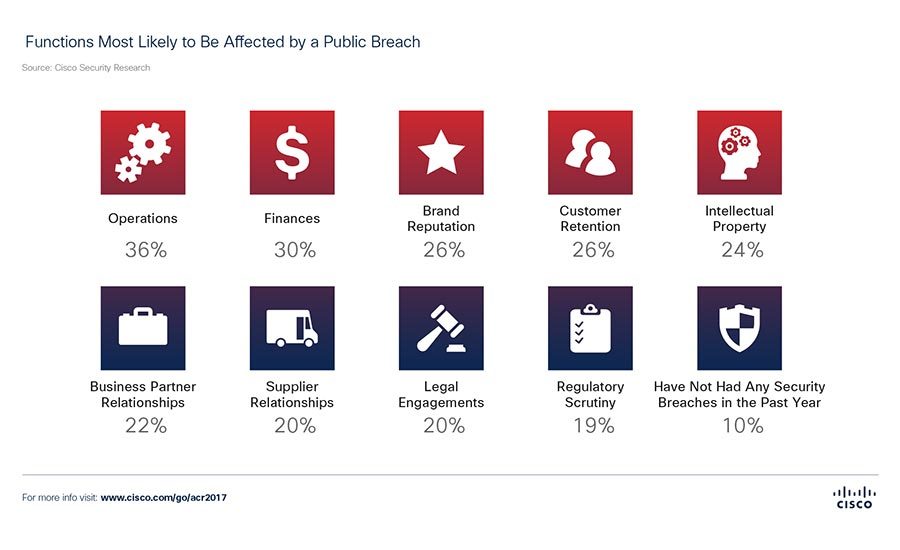
Source: Security Magazine
It is no secret how devastating a successful cyberattack can be. According to IBM’s 2023 Cost of a Data Breach Report, “the average impact of a data breach on an organization with fewer than 500 employees is $3.31 million; the average cost per breached record is $164.” Third party data breaches can be particularly damaging due to the involvement of external vendors, highlighting the importance of third party risk management. And, with a new report from Netwrix announcing that 68% of organizations suffered a cyberattack, it pays to take mitigation seriously and invest in identification and monitoring practices to protect your business.
What is third-party risk management?
Third-party risk management is done through a third-party risk assessment, also sometimes referred to as a vendor or supplier risk assessment. Which is a comprehensive evaluation of potential risks associated with each vendor relationship a business has established. This assessment aims to identify and analyze possible security risks such as data security, operational efficiency, regulatory compliance, financial stability, and reputational impact. Third party data breaches are a significant concern that TPRM seeks to address, as they can arise from business relationships with external parties. The assessment typically includes the review of documentation like contracts, security policies, and compliance certifications, as well as conducting audits and interviews.
The objective is to identify vulnerabilities susceptible to cyber threats or operational disruptions. Through a methodical process, organizations can deploy mitigation strategies, fortify their security posture, and safeguard business objectives from potential compromise brought on by third-party relationships.
Building a Strong Vendor Risk Management Program
Purpose of third-party risk assessments
Third party risk assessments aren’t meant to poke holes in a business’s security measures, but instead, help educate companies on possible risks that exist within their partnerships. Therefore, decisions can be made on how to fix the threat or terminate the relationship if necessary. As the business has grown to become more digital, companies are starting to dedicate more time and resources to their cybersecurity efforts.
Setting up vendor risk criteria
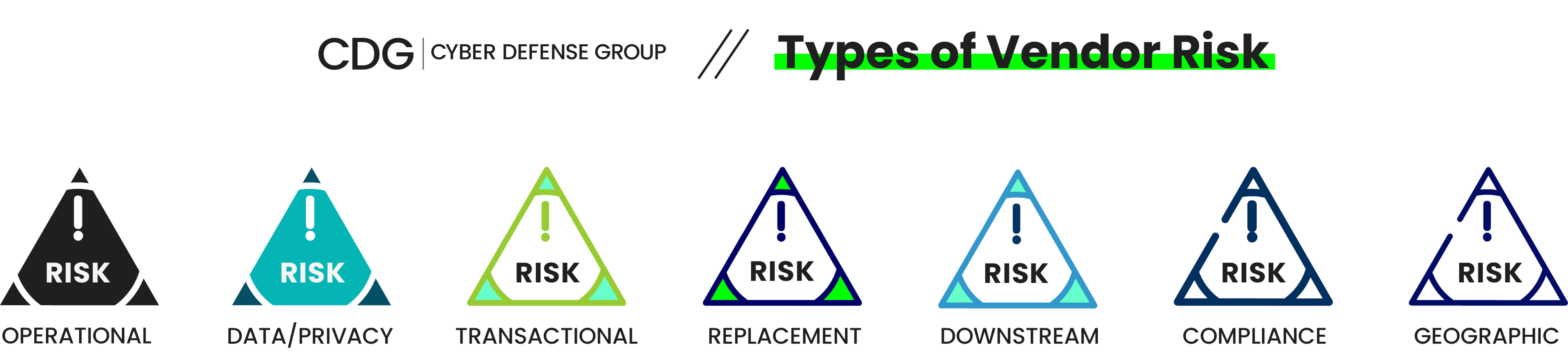
Several vendor risks are common across many industries. It is crucial to evaluate and prioritize these risks based on inherent risk scores, which consider industry benchmarks, business context, impact on operations, and contract value.
- Operational risk: Determine the importance of the vendor’s service in your organization’s business activities and operations.
- Data/privacy risk: Determine whether the vendor will handle or store critical information like customer, donor, or employee information.
- Transactional risk: Establish if the vendor will handle financial transactions for your organization.
- Replacement risk: Determine whether you can replace the vendor service if they come to a halt.
- Downstream risk: Determine if the vendor will use sub-contractors who might deliver certain services for your organization.
- Compliance risk: Ensure that the vendor complies with your organization’s regulations.
- Geographic risk: Determine the physical location of the vendor and if it is secure to deliver services for such locations.
Performing third-party onboarding and screening
Experts advise creating a formal structure for your third-party risk management program to standardize all third party onboarding and screening. Leveraging AI-powered platforms in third-party management can improve the accuracy of risk assessments and identify vulnerabilities in the digital supply chain. Businesses should also take comprehensive real-time risk-checking and containment methods to ensure a thorough third-party risk assessment.
Easy and manageable assessment
Your third party assessment should not be gruesome. A good assessment is thorough, informative, easy to understand, and comfortable to manage. It is crucial to build a comprehensive vendor risk management program that addresses all relevant types of risks. Understand that undertaking assessment is one of many tasks your vendor does, but it also ensures that critical information is collected.
Ensure your assessment is an ongoing process and not a one-time job. Create a process that ensures continuous supervision for vendors who might be risky.
Use technology as part of your risk assessment process
It’s prudent to utilize technology to aid your third-party risk assessment. Identifying and resolving critical cybersecurity issues within a company’s third-party ecosystem is essential for maintaining robust security. Technology and innovation assessment software helps a smooth and comprehensive vendor assessment process.
Utilizing technology for your assessment process has the following benefits:
- It offers you command over a system that allows you to frequently monitor any number of third parties and the hazards involved.
- It influences the scope of your evaluation while improving your capacity to anticipate and analyze internal and external third-party threats.
- It assists you in gathering and performing a macro-analysis of reliable data on third party risks across several assessments, which will improve any future vendor selections made by your company.
- It allows you to examine the effectiveness of risk assessment metrics, which identifies the caliber and dependability of your data.
Incident response plan in third party risk management

Another aspect of third-party risk management to consider involves your incident response plan. While many businesses have an Incident Response plan ready in case of a breach, often these plans lack true detail or actionable steps to follow when the breach is the result of an external vendor relationship. This is particularly crucial in the context of third party data breaches, which can significantly impact your cybersecurity posture. Little knowledge is known about the timeline that follows and what must be done. To proactively prepare, consider these key questions for constructing your incident response plan to address third-party risks:
- When should the third party vendor be notified of the breach?
- Who specifically within the vendor organization should be contacted?
- What information should be communicated to the vendor regarding the breach?
- How will the vendor’s role in the breach be addressed or mitigated?
- What steps will be taken to prevent future breaches in the vendor relationship?
Starting with these questions will enable your business to build a resilient incident response strategy capable of mitigating third-party risks effectively.
Conducting regular assessments
Managing third party risk is an every evolving moving target. By performing regular annual assessments of third-party risks or whenever a new vendor is onboarded, you help ensure your business can operate under the safest conditions. With more businesses seeking collaborations or outsourcing daily operations, avoiding third-party entanglements is increasingly complex. This necessitates businesses to internally or independently review all partnerships for self-preservation. During these regular assessments, a cybersecurity expert or team should scrutinize each external partnership, evaluating various aspects, including:
- Documentation management
- Licenses and certifications
- Insurance policies
- Network diagrams
Most auditors will employ a risk management framework from the International Organization for Standardization (ISO) or the National Institute for Standards and Technology (NIST) to analyze your third-party risk management program.
By leveraging these frameworks through regular assessments, you not only ensure thorough and accurate transparency, but also gain the peace of mind that your business is protected against the complex and evolving landscape of third-party risks.
Managing third-party risks in cybersecurity

In closing, managing third-party risks is crucial in today’s digital landscape, where cyber threats are increasingly sophisticated and pervasive. As businesses depend more on external vendors for efficiency and growth, the potential for security breaches and operational disruptions rises. Third party data breaches are a significant concern that needs to be managed, as they can lead to severe consequences for businesses. Effectively managing these risks protects sensitive data, ensures compliance, and maintains business continuity. While it may seem counterintuitive to bring in another third party to manage these risks, leveraging external expertise is prudent. Specialized third-party risk management firms have the knowledge, tools, and experience to identify and mitigate risks more effectively than most in-house teams. This strategic approach enhances an organization’s security posture and ensures that all potential vulnerabilities are comprehensively addressed.
If you’re looking for more guidance on how to complete third-party risk assessments or need immediate security assistance, Cyber Defense Group can help. We’re committed to building a more secure future for mid-market and enterprise companies. Your business innovation and growth are empowered with our services, helping you maintain a competitive edge in this digital age. Your protection is our priority.
Get in touch, and learn how Cyber Defense Group can help you manage your company’s third-party risk.
