The Importance of Cybersecurity Monitoring
Unknowingly joining the UIA
The creation of the Ukrainian IT army
On February 26, 2022, Mykhailo Fedorov, the Vice Prime Minister of Ukraine, announced the creation of an IT army to fight on the cyber front against threats to Ukraine. The Ukrainian IT Army (UIA) has been effective in taking down websites related to Russia’s state and private sectors through distributed denial of service (DDoS) attacks.
Misconfigured docker engines
CrowdStrike discovered two Docker images running on compromised Docker Engines, which were created to launch DoS attacks against Russian websites. The Docker Engines were running as legitimate honeypots but were misconfigured. The operators of these honeypots did not intend to participate in a cyber war against a nation-state, and this is where an ethical boundary was crossed.
Direct risk of Nation-State retaliation
Misconfigured systems are often hijacked for nefarious reasons, but the situation changes when there is a risk of nation-state retaliation. A nation-state retaliation could lead to lost revenue, a disruption of service, or a negative propaganda attack. There is a risk that if an environment with misconfigurations is targeted by a power such as the Russian GRU, the misconfigurations will be exploited, leading to a more disastrous outcome.
The need to monitor
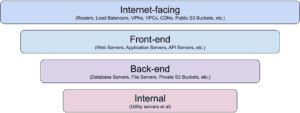
To prevent misconfigurations, monitoring is essential. Security information and event management (SIEM) solutions are fully mature solutions to this problem, but there are many things that can be done until that point. Cloud-based solutions offer data and monitoring out of the box that is commonly underutilized.
Using AWS EC2 monitoring capabilities
AWS’s EC2 monitoring capabilities offer great data regarding network activity in and out of a system, which can be vital yet constantly overlooked. AWS allows users to create alerts based on this data. If an EC2 instance running containers gets compromised and begins to send a slew of requests out, AWS will alert the user. Monitoring should be kept top of mind at every layer of the stack, and it is the responsibility of the engineer to understand the products they are using fully.
In order to effectively monitor and protect your infrastructure, it’s important to start with the basics and work your way up. A few simple steps you can take to begin implementing a monitoring strategy for your organization are:
Discover
Monitor
Alert
Start simply and slowly. Start with the outer layers of your infrastructure, look at what data you have available to you. Dig into the user interfaces (UIs) of the products and services and see what you have enabled, what you can enable, and what your options are. The more you understand about the products you’re using, the more options you’ll have in understanding your entire stack.
You can’t turn on alerts without knowing what to alert. Establish a baseline. Keep an eye on the data you have for a while. I tend to aim for at least a couple of weeks. If I have the option, I’ll email myself a daily report of the data for those two weeks so I can dig in and understand the trends. This step is the real meat of any machine learning (ML) tech within a SIEM. That’s the convenience they’re offering you and what you’re really paying for. But if you’re not at that place, you can still do it manually ― you just need to understand your baseline numbers.
Based on your baseline, you can now configure alerts at thresholds that make sense for you. If there is enough of a departure from the trends you’ve seen, you should know about it. This gives you the opportunity to investigate why that departure occurred and discover any potential issues; for instance, a rogue container attacking a foreign nation-state.
Monitoring can be huge and expensive, but it can absolutely be small and bootstrapped. Don’t wait until you have the budget for the SIEM. Get it in place from the start.
-
The Equifax data breach
The Equifax data breach in 2017, which affected millions of individuals and exposed sensitive personal information, highlights the critical importance of cybersecurity monitoring for detecting vulnerabilities and threats.
-
The SolarWinds supply chain attack
The SolarWinds supply chain attack in 2020 demonstrated the need for cybersecurity monitoring not only within an organization but also across the entire supply chain to prevent sophisticated and coordinated attacks.
-
2019 Capital One data breach
The 2019 Capital One data breach underscores the importance of regular testing and monitoring of cybersecurity defenses to identify and address vulnerabilities before they can be exploited by hackers.

