Difference Between ISO 27001 and SOC 2: Battle of Compliance Standards

Organizations frequently encounter a sense of overwhelm when navigating the vast security landscape and its multitude of threats. To proactively mitigate potential risks, it is crucial to adhere to well-established security frameworks like SOC 2 (System and Organization Controls) and ISO/IEC 27001:2013 (International Organization of Standardization/ International Electrotechnical Commission). By doing so, organizations can effectively fortify their security posture and ensure robust protection against evolving threats. A formal internal audit process, known as a compliance audit, is a mandatory component of ISO 27001, as per the standard’s clause 9.2. While every business has unique needs, implementing uniform security practices is essential. While compliance isn’t synonymous with security, it’s a significant step towards demonstrating a commitment to SOC 2 compliance or ISO 27001 and instilling client confidence in your security measures.
Understanding the key differences
Safeguarding your organization from cyber threats should be a top priority for any business. Safeguarding your business requires choosing the right security certification. In today’s security landscape, two standout certifications within the security framework are SOC 2 compliance and ISO 27001. To achieve SOC 2 compliance, companies need to hire an external auditor through a CPA firm that is licenced to complete the review and issue an attestation report.

These certifications provide essential frameworks for data and system protection. SOC 2 Type 2 focuses on how information security management systems, controls and processes for customer data security, availability, processing integrity, confidentiality, and privacy. ISO 27001 is an internationally recognized standard for establishing and maintaining an information security management system.
When choosing between SOC 2 compliance vs ISO 27001, consider your organization’s specific security needs, objectives, and priorities. SOC 2 Type 2 certification is preferred by service organizations that store customer data, demonstrating their commitment to high security standards to protect that data. ISO 27001 provides comprehensive coverage of various security aspects, making it suitable for organizations prioritizing a holistic approach to information security management.
Security controls: SOC 2 vs ISO 27001
Understanding the benefits and nuances of SOC 2 compliance vs ISO 27001 certifications, including the audit scope, helps make an informed decision aligned with your organization’s needs. Consider industry requirements, customer expectations, and desired security maturity level. Both certifications hold substantial value in today’s world and significantly enhance your organization’s security posture. Choose wisely to protect your business effectively.
Overview: SOC 2
Let’s talk about SOC 2 Type 2. A SOC 2 Type 2 audit can be needed for a variety of reasons, such as when you are undergoing a merger, acquisition, or licensing agreement, and it often starts with a compliance readiness assessment. It is an industry-leading security and compliance standard that focuses on the protection of data and information systems, usually beginning with a Compliance Readiness Assessment.

SOC (Service Organization Control) Type 2 is a certification developed by the American Institute of Certified Public Accountants (AICPA) that verifies an organization’s security controls over a specific period of time. It can be applied to the entire organization or to a specific system or service. The primary focus of a SOC 2 Type 2 audit is to ensure the security of customer data. There are five of the Trust Services Criteria within SOC 2 Type 2: Security, Availability, Privacy, Confidentiality, and Processing Integrity. While Security is mandatory for all organizations, additional Trust Services Criteria may be included based on the organization’s client base and operations.
Once a SOC 2 Type 2 audit is successfully completed, a reputable CPA firm rigorously evaluates the organization. Upon completing the audit scope, the organization receives an attestation report. This comprehensive document provides detailed insights into the organization’s adherence to industry standards and best practices. Valid for one year, the report serves as tangible proof of the organization’s unwavering commitment to safeguarding that data and ensuring its utmost security. It highlights measures like robust security protocols, vulnerability assessments, and risk management strategies. With this report, the organization can confidently demonstrate its high standards of data protection and a secure environment for valuable information to stakeholders and clients.
High-level overview: SOC 2
- Focus on customer data protection: SOC 2 is set up to protect customer data, available, processed correctly, and kept confidential and private.
- Trust Services Criteria: Evaluates an organization based on five SOC 2 Trust Principles, or Trust Services Criteria (TSC).
- Service organizations: Primarily aimed at organizations that store or process data from customers.
- External audits: Requires an external auditor from a licensed CPA firm to conduct the review and issue an attestation report.
- Annual attestation: Certification is valid for one year and needs annual re-evaluation.
- Tailored controls: Allows organizations to tailor their security controls to meet specific client requirements and business needs.
Overview: ISO 27001
What is ISO 27001? ISO 27001 is an international standard for data protection created jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). This framework outlines the requirements to establish, maintain, and continually improve an information security management system (ISMS). Many companies look to the 27001/27002 standards created by the International Organization for Standardization as the basis for their method of organizational controls.
ISO 27001 certification may be crucial for businesses needing to comply with information security-related legal, statutory, or regulatory requirements. It provides a systematic approach to effectively managing all sensitive data, pinpointing potential risks, and implementing effective controls to mitigate them.
To attain ISO 27001, begin your compliance journey by conducting a risk assessment, establishing and enforcing security controls, regularly evaluating their efficacy, and working with a certification body.
High-level overview: ISO 27001
- Globally recognized standard: ISO 27001 is a comprehensive framework for information security management.
- Risk management: Involves identifying and mitigating potential risks.
- ISMS implementation: Establishes, implements, and maintains an Information Security Management System (ISMS).
- Internal audits: Requires a formal internal audit process (clause 9.2).
- Suitable for all sizes and industries: Applicable to organizations of various sizes and sectors.
- External certification: Achieved through external audits, ensuring compliance with legal and regulatory requirements.
Ensuring data security: ISO 27001 vs. SOC 2

Processing integrity plays a key role in both ISO 27001 and SOC 2, making sure that systems do what they’re supposed to do accurately and reliably, thereby enhancing the overall security posture. In ISO 27001, it’s part of the broader picture in the Information Security Management System (ISMS). This standard mandates robust policies, procedures, and controls to maintain accurate, complete, and valid data processing. This standard mandates robust policies, procedures, and controls to keep data processing accurate, complete, and valid. By conducting regular risk assessments and internal audits – as ISO 27001 demands – we can spot and tackle any threats to processing integrity.
On the flip side, when it comes to SOC 2, processing integrity is a big deal among its five Trust Services Criteria. This part basically looks into whether a system does what it’s supposed to do in the right way, at the right time, and without missing anything. During SOC 2 audits, they check how well controls for system operations work, like spotting errors, fixing them, and making sure data is accurate. SOC 2 focuses on these things to make sure systems handling client data keep up high levels of integrity, which in turn builds trust and reliability in the services offered. Both frameworks stress how crucial processing integrity is, just in their own unique ways and scopes.
Similarities and differences between ISO 27001 and SOC 2
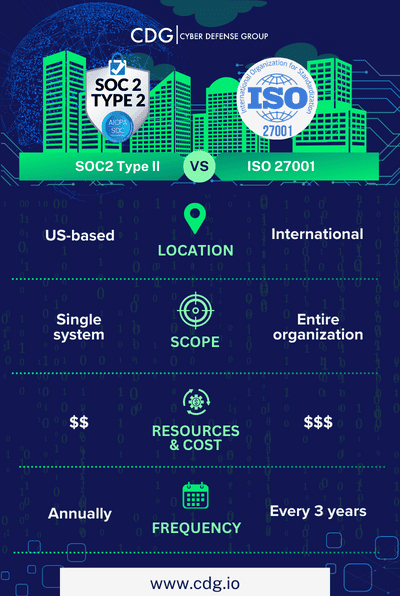
Infographic comparison overview of SOC2 vs ISO27001.
ISO 27001 is a complex standard that may not suit all organizations, especially mid-market ones. Implementation can be lengthy and resource-intensive. Keeping up with this standard’s evolving demands may pose challenges.
Despite differences, ISO 27001 and SOC 2 share many similarities when it comes to security controls. A study found that up to 96% of controls overlap. Differences depend on certification scope, trust services criteria, and business type. The key lies in the controls you choose to implement.
Comparison overview of the two security frameworks
Both frameworks aim to provide robust protection and have a lot in common, particularly in enhancing security maturity. When you’re gauging how well they keep your systems and data safe, think about these important factors:
- Focus: SOC 2 emphasizes customer data protection; ISO 27001 provides a comprehensive approach to information security management.
- Applicability: SOC 2 is primarily for service organizations; ISO 27001 is suitable for organizations of all sizes and industries.
- Criteria: SOC 2 uses five Trust Services Criteria; ISO 27001 requires establishing an Information Security Management System (ISMS).
- Audits: SOC 2 requires external audits by a licensed CPA firm annually; ISO 27001 involves a formalized internal audit process and periodic external audits.
- Flexibility: SOC 2 allows tailored controls for specific client needs; ISO 27001 mandates a structured, organization-wide approach.
- Certification duration: SOC 2 certification is valid for one year; ISO 27001 certification is valid for three years with annual surveillance audits.
Considering key factors like the threat level, IT complexity, security breaches, and regulatory needs helps you make informed choices in selecting a security framework. This ensures a solution that meets current needs while being scalable for future challenges. Assessing these factors helps build a strong security strategy to protect assets and mitigate threats.
Can you get your ISO 27001 and SOC 2 at the same time?

Yes, it is possible to obtain both ISO 27001 and SOC 2 certifications concurrently. By implementing controls that align with one of the standards, organizations can effectively address the requirements of the other due to the significant overlap in controls. This approach not only streamlines the certification process but also enhances the overall information security management system and risk assessment posture of the organization. By adopting a comprehensive approach that covers both ISO 27001 and SOC 2, companies can demonstrate their commitment to robust information security practices and provide assurance to clients and stakeholders regarding the protection of sensitive data.
Use cases for versatility and benefits
SOC 2
- Cloud service providers: Companies offering cloud-based services use SOC 2 to assure clients that their data is secure, available, and handled with confidentiality.
- Technology and SaaS companies: Businesses in the tech sector, especially those dealing with data from customers, benefit from SOC 2 compliance by demonstrating strong security around data practices.
- Financial services: Financial organizations use SOC 2 to show they have stringent controls and security protocols in place for managing customer data and transactions.
- Healthcare providers: Healthcare organizations adopt SOC 2 to ensure compliance with industry standards for protecting patient information and meeting HIPAA requirements.
- Third-Party vendors: Vendors that handle sensitive data for clients often need SOC 2 compliance to build trust and validate their security practices to potential clients.
ISO 27001
- Large enterprises: Multinational corporations implement ISO 27001 to establish a comprehensive information security management system that protects sensitive information across global operations.
- Government and public sector: Government agencies and public sector organizations use ISO 27001 to meet regulatory requirements and safeguard citizen data.
- Manufacturing and industrial companies: Firms in these sectors adopt ISO 27001 to protect intellectual property and ensure the security of their operational technology.
- Financial institutions: Banks and financial institutions leverage ISO 27001 to manage risk, protect financial data, and comply with international regulatory standards.
- Consulting and professional services: Companies providing consulting or professional services implement ISO 27001 to protect client data and enhance their reputation for data security.
Key takeaways
SOC 2 Type 2 is ideal for companies that operate in the mid-market segment, providing a comprehensive framework to assess and report on the effectiveness of their security controls. ISO 27001 is suitable for organizations of all sizes and industries, as it offers a globally recognized standard for information security management. Both standards focus on different aspects of cybersecurity; SOC 2 emphasizes service providers’ controls and processes, while ISO 27001 focuses on the overall information security management system. Companies that handle sensitive data and have a large number of clients or customers may benefit from obtaining both certifications to demonstrate their commitment to protecting data at all levels.
Both certifications enhance an organization’s security posture, build client trust, and help meet regulatory requirements, but choosing the right one depends on the specific needs and context of the organization. Implementing these certifications involves adopting robust security measures. Keep in mind that comprehensive documentation and employee awareness training are necessary for both. Additionally, ISO 27001 requires a formalized internal audit processes as per the standard’s clause 9.2.
Conclusion
In conclusion, when it comes to deciding between SOC 2 vs ISO 27001, the choice depends on your organization’s specific needs, resources, and other security objectives. Both these frameworks provide robust systems for ensuring cybersecurity, but their focus and implementation requirements can differ. It’s crucial to thoroughly evaluate your organization’s cybersecurity needs and align them with the appropriate framework.
Takeaway: Both SOC 2 and ISO 27001 are excellent compliance efforts for organizations to undertake and can be utilized to gain advantages over market competition, demonstrate the design and operating effectiveness of internal controls, and to achieve compliance within regulatory requirements. Is one better than the other? I don’t think so and I don’t believe it’s always practical to look at it in that respect.
Remember, the journey towards cybersecurity maturity is not a one-time effort, but an ongoing process that requires commitment, vigilance, and adaptation to evolving threats. Whether you choose SOC 2 Type 2 or the ISO 27001 certification, the ultimate goal is to protect your organization and your customers’ data.

Looking for a trusted partner in your journey toward cybersecurity maturity?
At the Cyber Defense Group, our team of experts is committed to walking beside you on your journey towards cybersecurity maturity. With a deep understanding of both SOC 2 and ISO 27001 frameworks, we provide customized solutions that align with your unique business needs, resources, and objectives by identifying which security controls are appropriate for your organization and take the necessary steps to implement them. Our goal is not just to help you implement these frameworks but also to ensure their effectiveness in protecting your organization’s compliance and your customers’ data. So whether you’re leaning towards the SOC 2 Type 2 or ISO 27001, you can be confident in our ability to support your needs. Trust us to be your reliable partner in achieving cybersecurity excellence, let’s take the first step in your compliance needs together.
Want to learn more?
Schedule a free consultation today with one of our cybersecurity experts to learn more!
